Hosting a Secure Static Website with S3 and CloudFront: Part IIa
Overcoming Challenges in AWS Automation: Lessons from Deploying a Secure S3 + CloudFront Static Website
Introduction
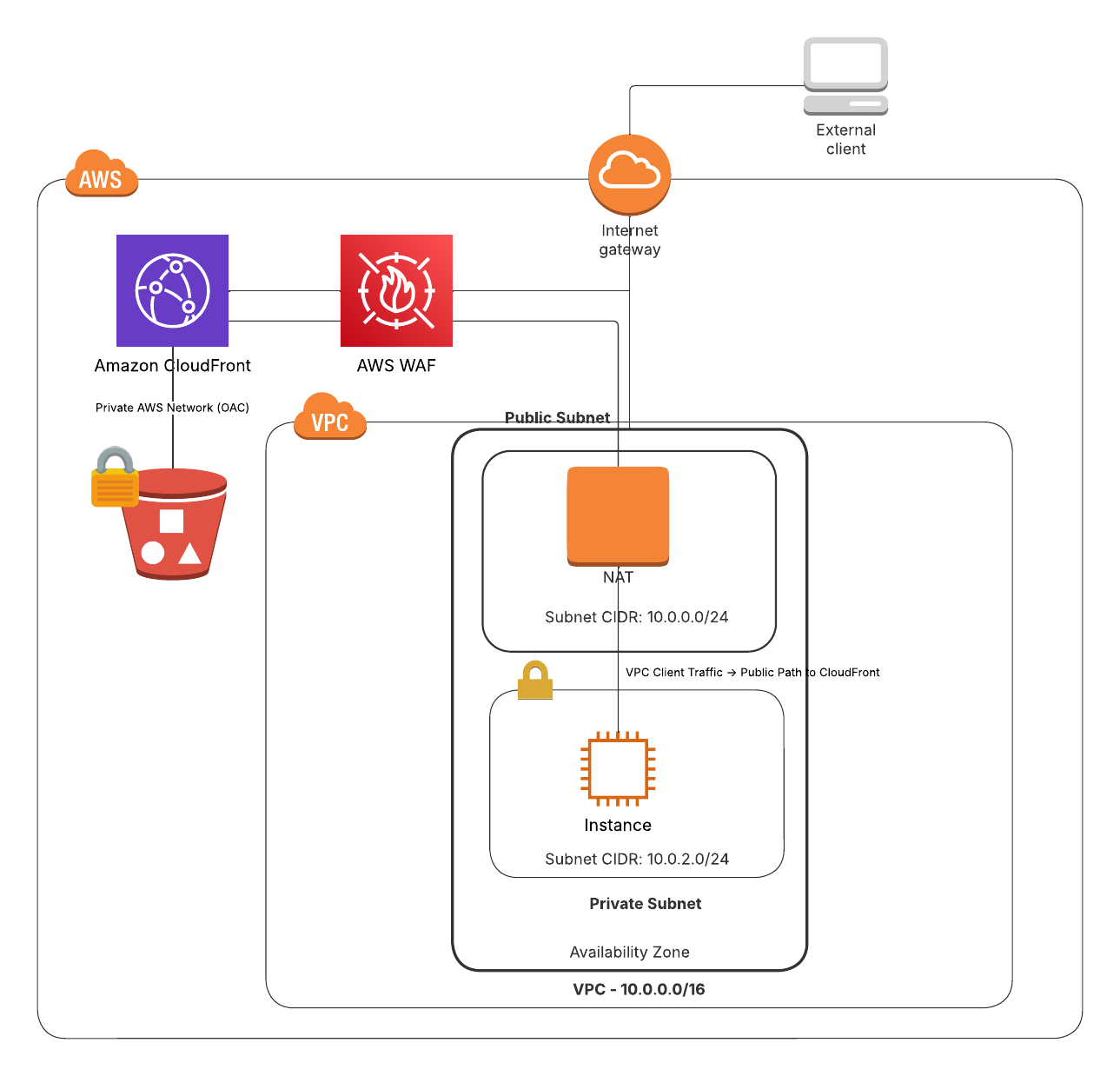
After designing a secure static website on AWS using S3, CloudFront, and WAF as discussed in Part I of this series, we turned our focus to automating the deployment process. While AWS offers powerful APIs and tools, we quickly encountered several challenges that required careful consideration and problem-solving. This post explores the primary difficulties we faced and the lessons we learned while automating the provisioning of this infrastructure.
1. Service Interdependencies
A key challenge when automating AWS resources is managing service dependencies. Our goal was to deploy a secure S3 website fronted by CloudFront, secured with HTTPS (via ACM), and restricted using WAF. Each of these services relies on others, and the deployment sequence is critical:
- CloudFront requires an ACM certificate
- before a distribution with HTTPS can be created.
- S3 needs an Origin Access Control (OAC)
- configured before restricting bucket access to CloudFront.
- WAF must be created and associated with CloudFront
- after the distribution is set up.
Missteps in the sequence can result in failed or partial deployments, which can leave your cloud environment in an incomplete state, requiring tedious manual cleanup.
2. Eventual Consistency
AWS infrastructure often exhibits eventual consistency, meaning that newly created resources might not be immediately available. We specifically encountered this when working with ACM and CloudFront:
- ACM Certificate Validation:
- After creating a certificate, DNS validation is required. Even after publishing the DNS records, it can take minutes (or longer) before the certificate is validated and usable.
- CloudFront Distribution Deployment:
- When creating a CloudFront distribution, changes propagate globally, which can take several minutes. Attempting to associate a WAF policy or update other settings during this window can fail.
Handling these delays requires building polling mechanisms into your automation or using backoff strategies to avoid hitting API limits.
3. Error Handling and Idempotency
Reliable automation is not simply about executing commands; it requires designing for resilience and repeatability:
- Idempotency:
- Your automation must handle repeated executions gracefully. Running the deployment script multiple times should not create duplicate resources or cause conflicts.
- Error Recovery:
- AWS API calls occasionally fail due to rate limits, transient errors, or network issues. Implementing automatic retries with exponential backoff helps reduce manual intervention.
Additionally, logging the execution of deployment commands proved to be an unexpected challenge. We developed a run_command function that captured both stdout and stderr while logging the output to a file. However, getting this function to behave correctly without duplicating output or interfering with the capture of return values required several iterations and refinements. Reliable logging during automation is critical for debugging failures and ensuring transparency when running infrastructure-as-code scripts.
4. AWS API Complexity
While the AWS CLI and SDKs are robust, they are often verbose and require a deep understanding of each service:
- CloudFront Distribution Configuration:
- Defining a distribution involves deeply nested JSON structures. Even minor errors in JSON formatting can cause deployment failures.
- S3 Bucket Policies:
- Writing secure and functional S3 policies to work with OAC can be cumbersome. Policy errors can lead to access issues or unintended public exposure.
- ACM Integration:
- Automating DNS validation of ACM certificates requires orchestrating multiple AWS services (e.g., Route 53) and carefully timing validation checks. We did not actuall implement an automated process for this resource. Instead, we considered this a one-time operation better handled manually via the console.
Lessons Learned
Throughout this process, we found that successful AWS automation hinges on the following principles:
- Plan the dependency graph upfront:
- Visualize the required services and their dependencies before writing any automation.
- Integrate polling and backoff mechanisms:
- Design your scripts to account for delays and transient failures.
- Prioritize idempotency:
- Your infrastructure-as-code (IaC) should be safe to run repeatedly without adverse effects.
- Test in a sandbox environment:
- Test your automation in an isolated AWS account to catch issues before deploying to production.
- Implement robust logging:
- Ensure that all automation steps log their output consistently and reliably to facilitate debugging and auditing.
Conclusion
Automating AWS deployments unlocks efficiency and scalability, but it demands precision and robust error handling. Our experience deploying a secure S3 + CloudFront website highlighted common challenges that any AWS practitioner is likely to face. By anticipating these issues and applying resilient practices, teams can build reliable automation pipelines that simplify cloud infrastructure management.
Next up, Part IIb where we build our script for creating our static site.
Disclaimer
This post was drafted with the assistance of ChatGPT, but born from real AWS battle scars.
If you like this content, please leave a comment or consider following me. Thanks.

 www.linkedin.com/in/robert-lauer-1590513
www.linkedin.com/in/robert-lauer-1590513